I’ve been investigating cloud native virtualization technologies in the past week. More specifically, I tried to:
- create/poweron/ssh into/poweroff/delete a virtualmachine by using qemu/kvm;
- create/poweron/ssh into/poweroff/delete a virtualmachine through libvirt+esxi;
- create/poweron/ssh into/poweroff/delete a virtualmachine through libvirt+qemu/kvm;
- create/ssh into/suspend/delete a container through libvirt+lxc;
- try out kata-container by following its quickstart guide:
- build the kernel;
- build the rootfs;
- add kata-container as an extra runtime to docker;
- run docker to start a container through kata-container so the container is actaully running as a vm;
- only qemu/kvm is used;
- try out firecracker by following its quickstart guide which basically boots up a vm by using provided kernel and rootfs;
- try out ignite by following its quickstart guide to import a kernel from a docker image, and deploy a container vm, ssh into it and delete it;
- also read some documentations on:
- kubevirt
- virtlet
After which, I get a rough idea of:
- what is libvirt;
- how is kubevirt, virtlet architectured and using libvirt;
- what is kata-container, firecracker, cloud-hypervisor, qemu/kvm, lxc/lxd;
To summary:
- kubevirt and virtlet all leverage libvirt to provision vms. They are mainly using the qemu/kvm mode for libvirt;
- kubevirt includes an operator, a handler per K8s node and a launcher per
vm; - virtlet instead implements a CRI proxy which calls virtlet process to provision the
vm besides the inband call to docker;
- kubevirt includes an operator, a handler per K8s node and a launcher per
- firecracker now provides a binary that allows you to boot a microvm with provided kernel and rootfs fast. It opens up a socket and listens of REST requests;
- ignite is a thin wrapper over firecracker as far as I call tell, including the abilities to easily manage kernel images, rootfs in an organized, docker-image way. But it’s not OCI-compliant, so it can only be used standalone now. Besides, it seems it’s integrated with weave net cni by default;
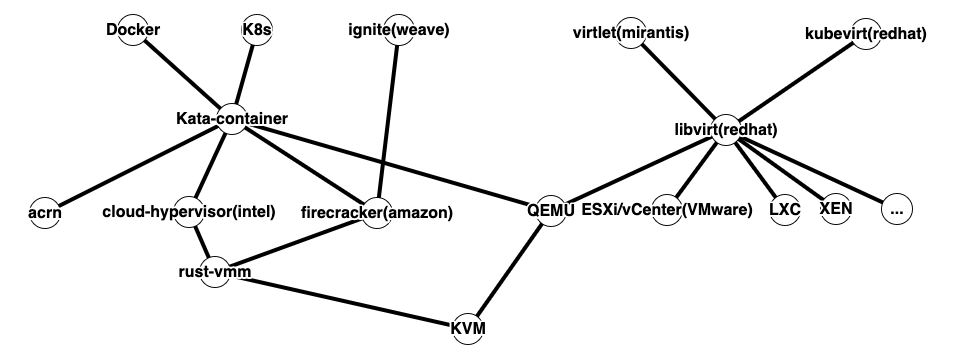
- kata-container is pretty well interfaced compared with ignite. It’s a OCI-compliant container runtime so it can be easily swapped in to replace runc in docker, also through cri-o, it can also be used in K8s as the runtime. On the backend, it leverages virtcontainer library to abstract Hypervisor calls into an interface. qemu/kvm, cloud-hypervisor, firecracker, acrn are supported now according to the doc;
- cloud-hypervisor and firecracker are built based on rust-vmm library, which includes many useful components to build vmm quickly, effectively and securely. Among them, it includes a kvm ioctl wrapper: kvm-bindings.
All my findings are recorded into my personal wiki and I’ll see if I can host it somewhere.
The following picture demonstrates their relationships: